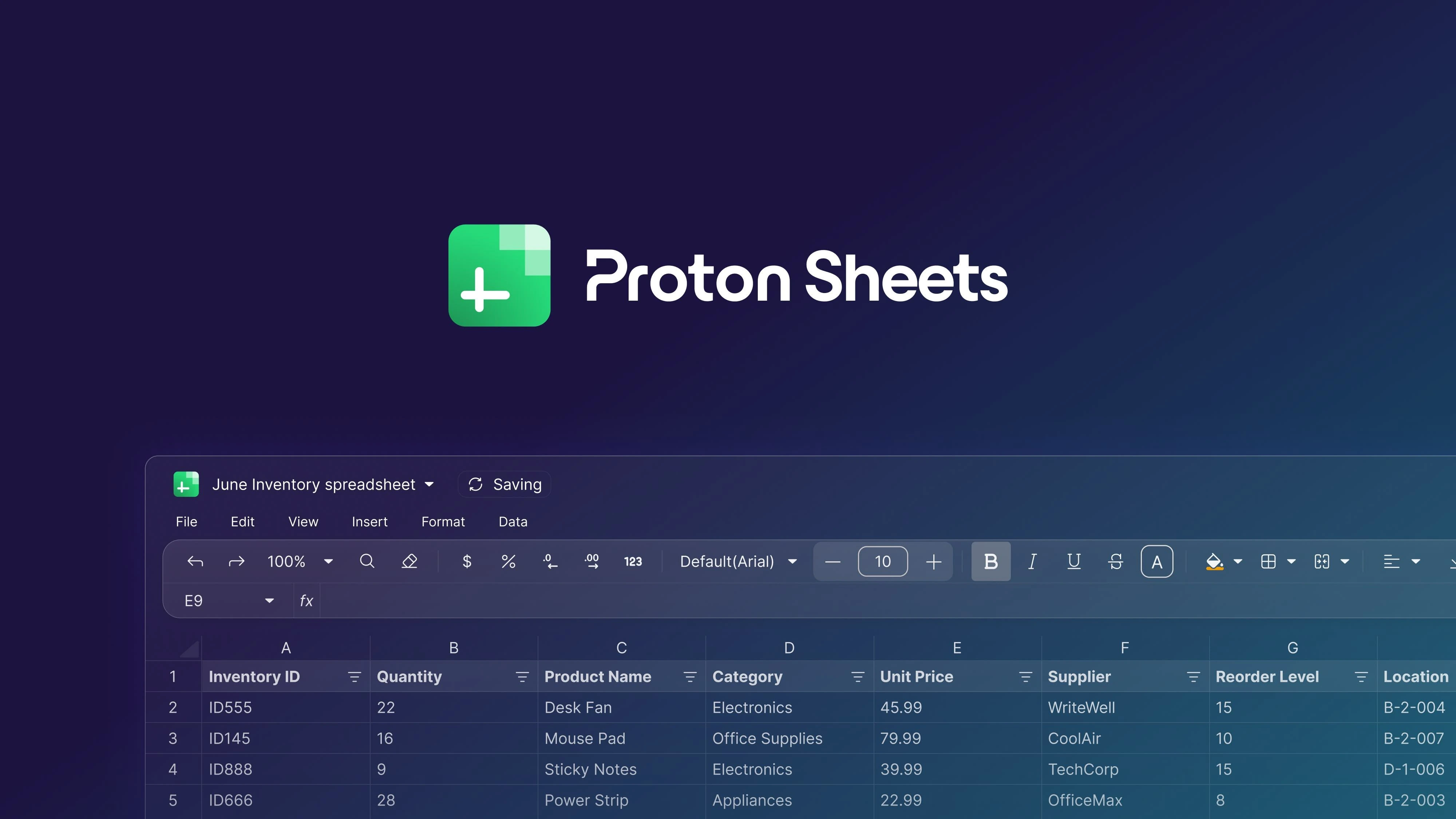
Proton Sheets: Bringing Zero-Access Encryption to Cloud Spreadsheets
For years, the power of cloud productivity has come with a mandatory trade-off: your data privacy. Whether you’re using Microsoft 365 or Google Workspace, sensitive business figures, financial plans, and personal records stored in spreadsheets are only protected by at-rest and in-transit encryption. This means the service provider—Google or Microsoft—can still access and scan your data.
Proton, the Swiss-based company that built its reputation on the world’s largest encrypted email service, is finally closing this critical security gap with the launch of Proton Sheets. This new tool is engineered from the ground up to offer robust, feature-rich spreadsheet functionality combined with the highest standard of end-to-end encryption (E2EE).
Why End-to-End Encryption is a Game Changer for Spreadsheets
In the context of cloud services, E2EE ensures that the data is encrypted on your device before it ever leaves, and it can only be decrypted by the intended recipient (or yourself) using a private key. Critically, Proton itself has zero-access to your information.
This approach offers unparalleled security benefits:
- Zero-Knowledge Protection: Proton, its employees, or any third party cannot read the contents of your spreadsheet, even if they were compelled to by a court order.
- Encrypted Metadata: Unlike many competitors that protect the content but expose the file name or modification date, Proton Sheets also encrypts crucial metadata.
- Protection Against Breaches: In the event of a successful attack on Proton’s servers, the stored data would be rendered useless to attackers without the decryption key.
Design and Core Functionality
Proton Sheets is designed to be instantly familiar to users migrating from Google Sheets or Excel, ensuring the learning curve is minimal. It provides a clean, modern interface and support for the essential features required for professional and personal use.
Key functional capabilities include:
- Formula Compatibility: Support for a large library of common mathematical, logical, and financial functions.
- Import/Export Flexibility: Seamless import and export of common formats like
.xlsxand.csvfiles, facilitating easy migration and sharing with non-Proton users. - Secure Collaboration: Protected sharing, which is a significant technical challenge for E2EE software. Proton’s infrastructure allows you to securely share and collaborate on sheets with other Proton users without compromising the encryption standard.
Proton Sheets vs. Mainstream Cloud Tools
The primary distinction between Proton Sheets and its established rivals is the privacy model. While Excel and Google Sheets offer powerful features and ubiquitous integration, they fundamentally operate on a trust model where you must trust the provider not to look at your data.
| Feature | Proton Sheets | Google Sheets / Excel Online |
|---|---|---|
| Data Encryption | Full End-to-End Encryption (E2EE). Zero-access architecture. | At-rest and In-transit encryption. Provider has access to data. |
| Privacy Model | Zero-Knowledge and Trustless. | Trust-Based (Relies on service provider policies). |
| Collaboration | Secure sharing only with verified Proton users. | Real-time collaboration with any user via link/email. |
| Data Location | Stored in Switzerland, protected by strict Swiss privacy laws. | Global data centers, subject to various jurisdictions (e.g., US CLOUD Act). |
Conclusion: A New Standard for Digital Productivity
The launch of Proton Sheets completes Proton’s fully encrypted productivity suite, which already includes Proton Mail, Proton Calendar, and Proton Drive. It signals a major step toward a future where users no longer have to sacrifice their privacy for the convenience and power of cloud computing.
For individuals and businesses handling sensitive information—from patient records and financial audits to confidential research—Proton Sheets provides a powerful, professional-grade solution. This new tool solidifies Proton’s position as the leading secure alternative for anyone looking to build a digital life that is fully protected from surveillance and data breaches.
Explore the Latest World of Technology.
Android
cross-device
file-explorer
phone-link
photos-tab
tech-news
windows-android
automation
bash-scripting
command-line
cron-jobs
file-permissions
linux-skills
terminal
vim
android-2026
android-security
apk-install
developer-verification
experienced-user
foss
google-play
open-source
sideloading
appimage